Have you ever been contacted by customer support on Telegram or Twitter asking you about your wallet or exchange account? Have you ever stumbled across a suspicious website that looks just like your regular exchange? These are all examples of common phishing attacks
Phishing is the most common way of bad actors teal funds in the cryptocurrency industry. Cases of Phishing attacks are growing. In fact, the average amount customers lost to phishing was 1900 dollars, which is 1000 percent more comparing to last year median. Being informed and aware of some of these attacks will make your experience interacting with crypto a lot safer.
Types of Phishing Attacks
Fake Customer Support Phishing
The most common type of phishing is a fake customer support approach where attackers pretend to be a part of a customer support team and request personal, sensitive and important information such as email, seed phrase and password. Scammers will be using similar usernames, images and will almost look identical to real customer support teams. Users seeking help from customer support become the main target for phishers, hence it is important to follow the instructions displayed on official sites and media. Most importantly customer support will never attempt to contact you first and they will never send you links or ask you for private information. When you get contacted in this manner immediately report the user and block them to stop the attack. You can always reach out to your exchange support team to verify if any requests are genuine.
Social Media Phishing
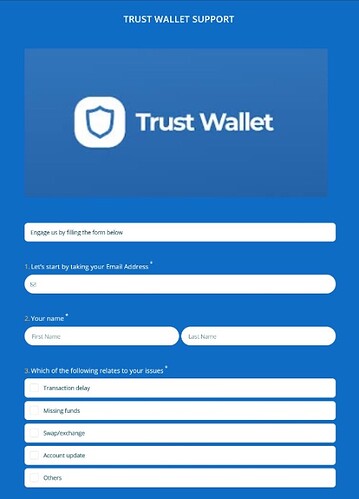
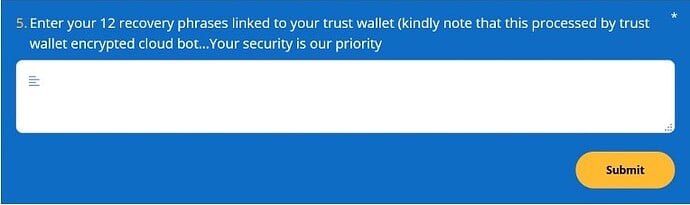
Trust Wallet users have recently been victims of targeted Twitter phishing attacks by pushing fake technical support forms. The recent phenomenon has been spotted by Lawrence Abrams who had been tracking a Twitter phishing scammer targeting Trust Wallet and Metamask users. Phishers respond to users’ tweets pretending to be from the Trust Wallet support team, who link them to phishing sites docs.google.com or forms.app links to fill out a support form and receive help.
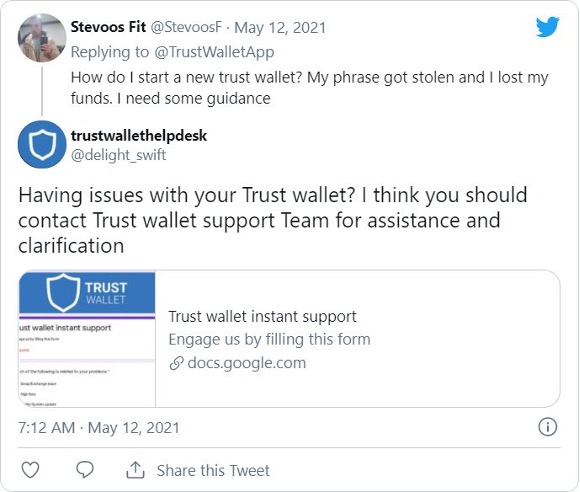
When users visit these links, they will be shown a page pretending to be a support form for Trust Wallet.
However, this will not be an ordinary form to fill as it will be asking you for your private information and most importantly your seed (recovery) phrase. We remind you never to share your seed phrase with anyone. This is the key to your coins.
SEO or Imposter Website Phishing
Scammers create a clone version of an original website; hence it is extremely hard to detect. These websites are more common to be the top hit on search using google and other engines found google Ads so that users do not suspect anything and enter sensitive information. Luckily, it is quite easy to spot fake sites. Simply check the URL of the website you intend to visit. Cloned websites will use similar looking but different letters such as “0” instead of “o” or “ä” instead of “a” as shown below. Most importantly, bookmark the original websites that are visited frequently to reduce risk completely.
Email Phishing
Email Phishing has been around since the 1990s and it is still widely used among phishers. The aim is still to steal your funds and information by emailing you directly. The perpetrators’ emails often use well-known apps name and will have a sense of urgency using words such as “few days” “now”. These emails will often include links and the email will be written in grammatically incorrect English. Take your time to look over all the details. Check the email source and the link in the emails as it will give you an indication if the email is fake. When everything points out to a phishing email, delete the email without opening it and block the user.
Fake Mobile Apps
Mobile users are not safe from phishing. There are many fake apps on Google Play and Apple Store many appear each day despite continuous efforts to ban them. The method appears to be particular popular on the Android platform. Thousands of users lost their funds to this type of phishing. For example, there had been many users scammed with a fake Cardano wallet which had a 4.3-star rating at a time. How do you recognise a fake app? Look for obvious misspelling, often the brand colours will be incorrect on the logo and brand name. Check for how many downloads were made for this app. Popular apps have a lot more downloads. Secondly, you can always check for the publishers’ name. Most importantly use an official link from the website of the exchange or wallet to install the app.
5 Recommendations on protecting yourself from Phishers
1. Never Share Your Recovery Phrase or Private Key with Anyone
The biggest take-home from this article is that you should never share your recovery (seed) phrase. Without the recovery phrase, scammers can do little to your funds. As soon as they have your recovery seed, they have full access to your crypto. Further never share any sensitive information such as your email address, passwords with anyone.
2. Do not click suspicious links
Do not click any links or embedded URL on suspicious websites and emails as they can be filled with malware. You can use CheckPhish services to check if a URL is safe to open.
3. Admins or Customer Support will not Contact you first!
When seeking help online from Customer Support or Admin be aware of perpetrators. Remember to follow legitimate instructions displayed on official websites. Moreover, when having an issue, an admin will never start a conversation with you over Facebook, Twitter or Telegram and ask for your recovery phrase. Most reputable exchanges and wallets have dedicated customer support emails ending in their official domain [email protected] and will only use these channels to contact you.
4. Be aware of third-party sites
Connecting your wallet to third-party sites is risky and makes you vulnerable to phishing. Do not attempt connecting with them before informing yourself of the right instructions. For instance, here is a guide on how to connect the DApps browser for Trust Wallet users.
5. Never trust alarming messages.
Reputable cryptocurrency companies will never urge you to submit personal information or to send funds to them or an outside party. Therefore, when such a message appears in your inbox, not in your spam folder do not open it or click any links, instead of block and delete such a message.
Conclusion
To conclude, it is each user’s responsibility to be safe in a crypto world. Scammers will always be out there and they will get smarter each day and develop new ways to steal funds and information from you. Each of us needs to be vigilant and safe stay. Let’s not let the fraudsters win.